Understanding Microsoft BizTalk Server
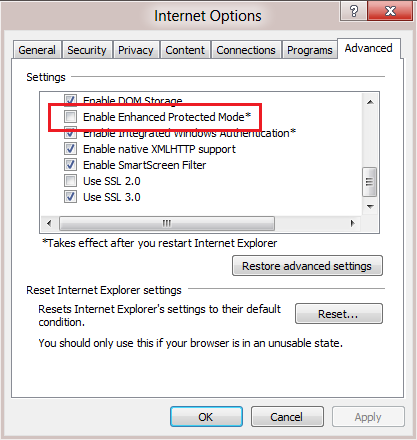
Understanding Business Integration Issues When organizations use the business-to-business and business-to-consumer commerce models when they use the Internet, they are faced with the following integrations issues: Application integration within the organization. Business integration over multiple organizations. While most businesses have different requirements for business process integration and data integration, businesses share a number of business …