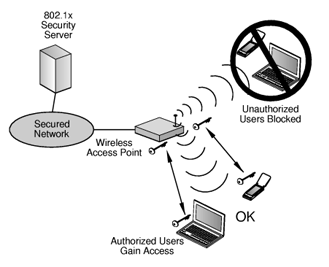
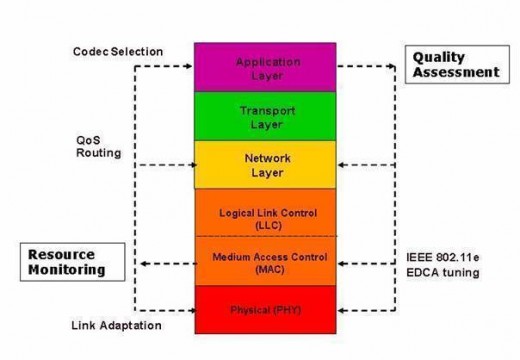
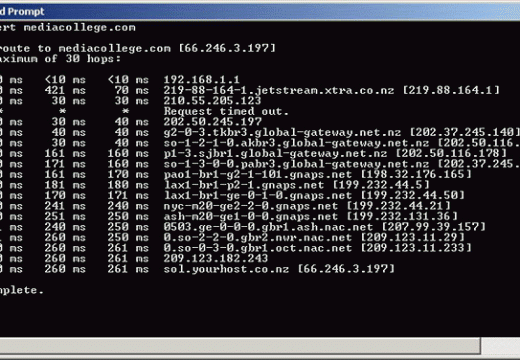
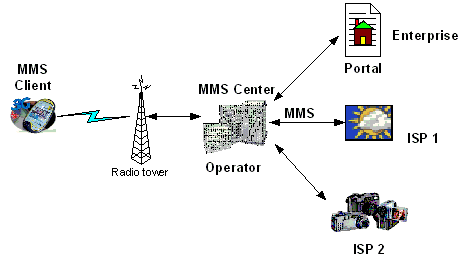
Public DNS Servers
DNS (Domain Name System) servers are designed to allow networked devices such as computers, phones, and other servers to look up address records in DNS tables. The majority of DNS servers are configured to provide service to the organizations or people that own or pay service fees for the hardware. There are a number of …