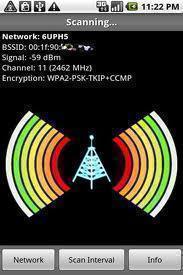
WiFi Signal Strength Meter
Windows and other operating systems have a WiFi signal strength meter, but this is usually basic software and does not really tell the user much about the wireless signal. Fortunately, there are many other programs that do the same thing, but show the user more details about the wireless connection. We will describe some of …