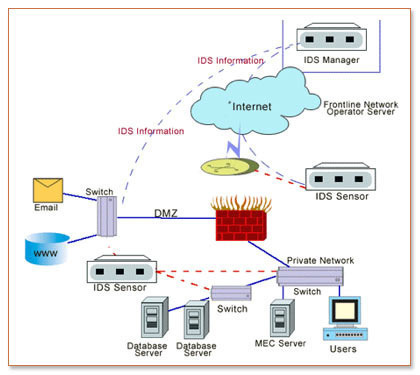
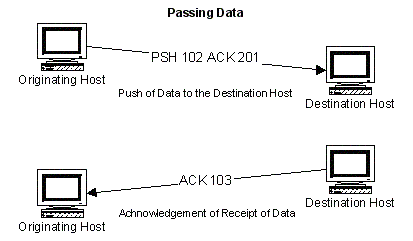
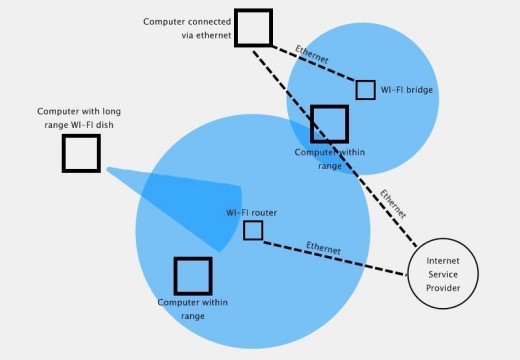
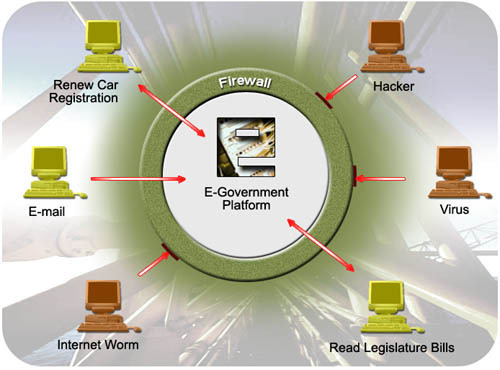
Intrusion Detection System (IDS)
Consumers commonly mistake an intrusion detection system (IDS)with a computer firewall. Although both applications have a similar goal to protect end-users from nefarious hackers and computer malware, an IDS differs from a firewall in that it can be either a device or software program created to monitor an individual computer, computing device, or network for …