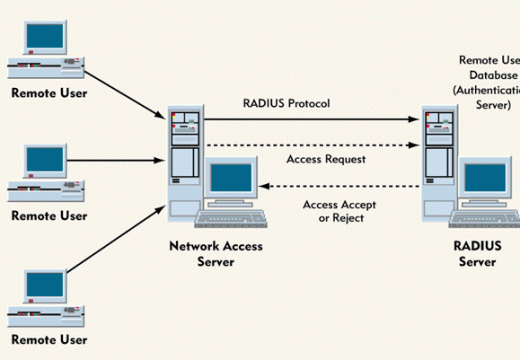
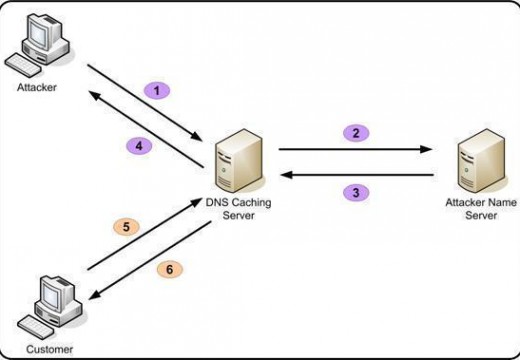
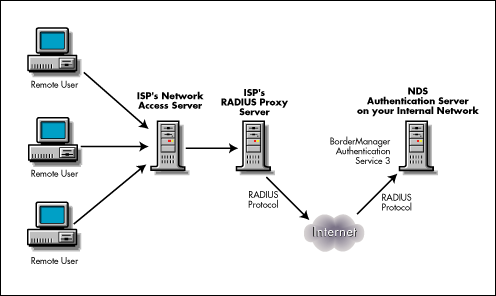
RADIUS Server
RADIUS (Remote Authentication Dial In User Service) is a system procedure that offers centralized entrance, approval, as well as accounting administration for individuals or computers to add and utilize a network service. Individuals often need “Authentication” when they try to fix to a network. People have to face far more problems while connecting their computers …