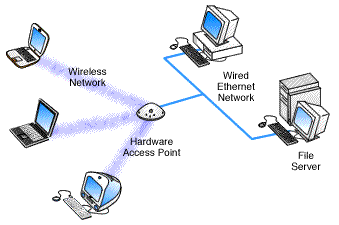
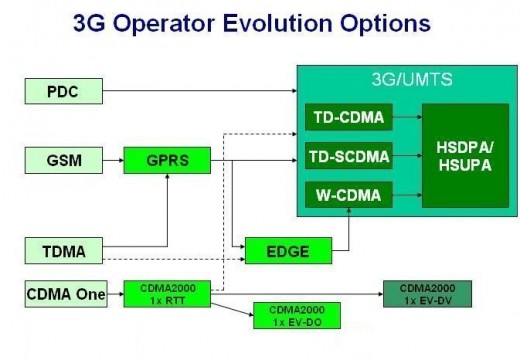
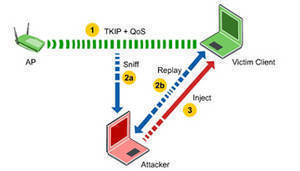
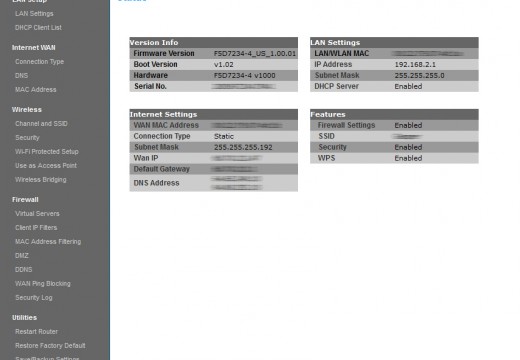
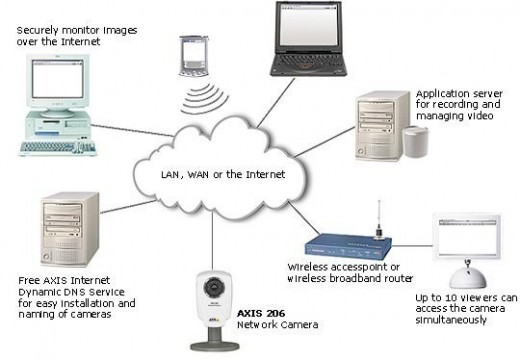
Access Point
As technology has advanced, devices have become more complex and integrated. Access points make a good example of such devices. These can be described as hardware that includes a modem, router, and other optional functions that are all compiled into one device. Access points are becoming more popular than modems or routers and they are …