MIC (Message Integrity Check)
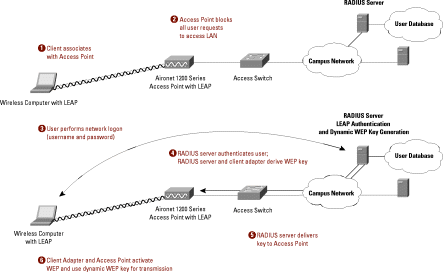
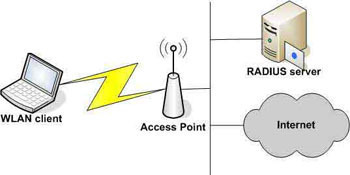
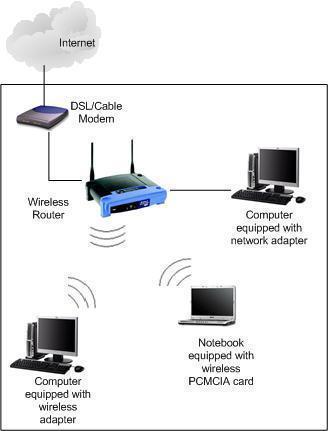
A message integrity check (MIC), is a security improvement for WEP encryption found on wireless networks. The check helps network administrators avoid attacks that focus on using the bit-flip technique on encrypted network data packets. Unlike the older ICV (Integrity Check Value) method, MIC is able to protect both the data payload and header of …