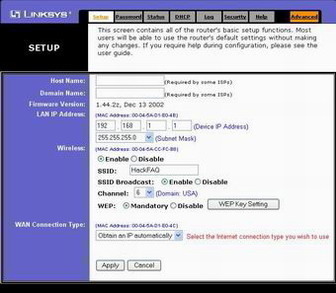
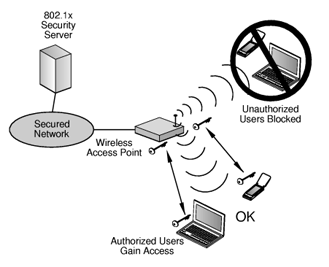
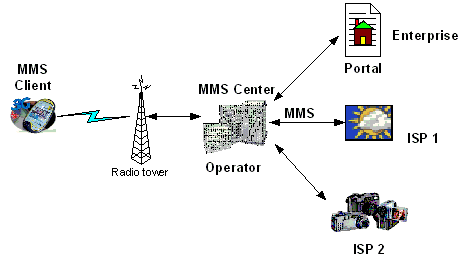
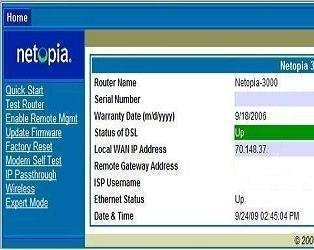
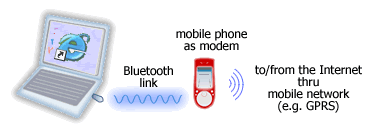
Wireless Routers
A wireless router is a wireless device that connects one computer or a whole network to another computer or network. It is possible to have a wireless network in a home or office. Travelers definitely come across wireless networks at most international airports. A wireless router, which is responsible for sending information from one computer …