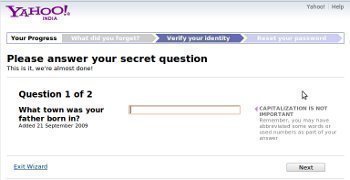
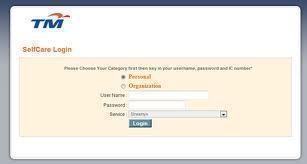
Cisco Password Recovery
“Physical access to a computer or router usually gives a sophisticated user complete control over the device. Software security measures can often be circumvented when access to the hardware is not controlled.” — Cisco Systems, Inc. Recovering the passwords for most Cisco devices via the console port is very simple. However, Cisco has purchased so …