Understanding Certificate Authorities
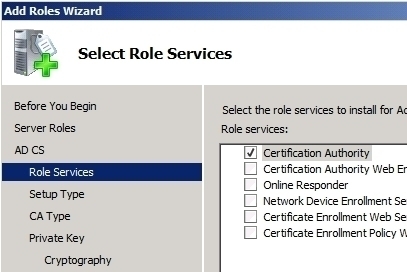
An Overview on Certificate Authorities In the Public Key Infrastructure (PKI), digital certificates are based on public key cryptography. The PKI consists of a set of components, policies, protocols, and technologies that provide data authentication, integrity, and confidentiality through the use of certificates, and public and private keys. Data is protected by applying a hashing …