Department of Defense Network (DoD) Network Model Introduction
Back in 1960, systems were primarily made up of mainframe computers, and were typically owned by fairly large companies and government institutions. Because mainframe computers run different proprietary software, and due to mainframes not being able to communicate between each other, special code (interface) had to be defined so that one mainframe could interrelate with a another mainframe. When an operating system changed between the two mainframes that were exchanging data, the interface had to be rewritten so that the two mainframes could communicate once more.
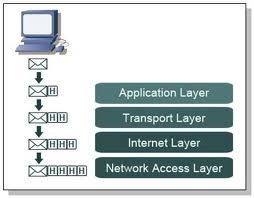
The network model which was created to enable users to exchange data between computer systems over a wide area network (WAN) is the Department of Defense (DoD) network model. The model is also referred to as the Defense's Advanced Research Projects Agency (DARPA) model.
The DoD model specifies the following four layers, which work collectively to form the basis for internetworking:
-
Network Interface layer
-
Internet layer or Internetworking layer
-
Host to Host or Transport layer
-
Application layer
A few characteristics of the DoD network model are:
-
Each specific layer of the DoD network model has its own functions
-
The different protocols in the Transmission Control Protocol/Internet Protocol (TCP/IP) protocol suite operate at different layers of the DoD model. Most networks today use TCP/IP to exchange data between networks and computers in a WAN. TCP and IP are collectively called the protocol stack or the network/transport protocols. This is due to the protocols operating at the Network and Transport layers to make it possible for computers to communicate.
The Network Interface Layer (layer one)
The Network Interface layer of the DoD model is layer one in the DoD model and is associated with the lowest level of the TCP/IP protocol. With reference to the Open Systems Interconnection (OSI) model of the International Organization of Standardization, the Network Interface layer of the DoD model is associated with its Layer 1 (Physical) and Layer 2 (Data-Link) capabilities. When compared to the OSI model, the DoD model's Network Interface layer provides almost the same abilities.
The hardware connected to the Network Interface is listed below:
-
Network medium: This is usually coaxial or twisted pair cabling. In networking today, wireless has become attractive.
-
Network interface card (NIC): The NIC has the following addresses:
-
MAC address, which is a physical address
-
IP address, which is a logical address
The NIC has a built-in circuit board and chips, and utilizes a driver. The driver, a software program, operates between the physical hardware and the operating system. In the OSI model, the NIC is works at Layer 1 (Physical) and Layer 2 (Data-Link). In the TCP/IP model, the NIC functions at Layer 1.
-
The Institute of Electrical and Electronics Engineers (IEEE) defines the common standards or specifications to implement network technology. For instance, the IEEE 802 specification defines the standards for the networking technologies which function at the Physical layer and Data-link layer. The standards defined differ, based on which network technology is used. TCP/IP however operates independently of the actual type of network.
The standards defined in the IEEE 802 specifications are:
-
802.1; the internetworking standards which pertain to managing local area networks (LANs) and metropolitan area networks (MANs). Included is the spanning tree algorithm used by bridges.
-
802.2; defines logical link control and dividing Layer 2 of the OSI model into two further sub-layers.
-
802.3; defines media access control for Ethernet networks, and frame formats for Ethernet.
-
02.4; specifies standards used for Token Bus networks that utilize 75ohm coaxial or fiber optic cabling. Included is the token passing access method.
-
802.5; for IBM's Token Ring technology which utilizes a physical star and logical ring topology using twisted pair cabling. Included is the token passing access method.
-
802.6; defines specifications for metropolitan area networks (MANs).
-
802.7; defines broadband transmissions which utilize Frequency Division Multiplexing (FDM). Included is CATV.
-
802.8; defines Fiber Optics networks. Included is Fiber Distributed Data Interface (FDDI) with the token passing access method.
-
802.9; defines integrated services over ISDN.
-
802.10; defines virtual private networks for securing communications over the Internet to the private network.
-
802.11; defines specifications for networking technologies. Included are the wireless communications methods 802.11a, 802.11b, and 802.11g.
-
802.12; defines specifications for the Hewlett Packard's 100VG Any LAN technology that utilizes the demand priority access method.
As the size of networks grew, it became more necessary to develop a standard method to control access to the shared media in order for communication to occur in a sequential manner. The Media Access Control (MAC) method performs the function of controlling and allocating access to the medium between network computers and devices. The various MAC protocols available for the many different communication technologies perform media access control.
The common media access control methods are:
-
Token Passing; utilized in Token Ring and FDDI networks
-
Carrier Sense Multiple Access/Collision Detection (CSMA/CD); utilized in Ethernet networks.
-
Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA); utilized in AppleTalk networks.
The Network Interface Card (NIC) uses hardware and software to connect a device to the network media. The different of NICs utilize unique connector types to connect to the physical medium. The different types of connectors are defined in the IEEE 802 specifications. The protocols which are used by NICs to perform receive, assemble, address and send data functions are specified in the TCP/IP Network Interface layer. The widely used Ethernet NIC utilizes Category 5 or greater unshielded twisted pair cable with pin connections. An Ethernet NIC receives, assembles, disassembles, and sends data over the network connection.
The Internet/Internetworking Layer (layer two)
The internetworking or Internet layer of the DoD model handles the packaging, addressing, and routing of data. The Internet layer of the DoD model relates to the OSI model's network layer. The Internet layer was initially defined to enable two computers to establish a connection to exchange data. The Internet layer formed the basis for internetworking or communication over the Internet. After the Network Interface layer receives data and translates it to signals on the physical medium, the Internet layer defines packaging, addressing, and routing of the data.
The main TCP/IP protocols that operate at the Internet layer are:
-
Address Resolution Protocol (ARP)
-
Internet Protocol (IP)
-
Internet Control Message Protocol (ICMP)
-
Internet Group Management Protocol (IGMP)
The Host to Host /Transport Layer (layer three)
The Host to Host, or transport layer of the DoD model manages the transportation of data, and establishes the connection between hosts to exchange already formatted data. This layer is associated with the Transport layer of the OSI model. The Host to Host layer is responsible for establishing communication channels between the Application layer and the lower layers.
The main CP/IP protocols that operate at the Transport layer are:
-
Transmission Control Protocol (TCP): TCP offers greater reliability when it comes to transporting data than what UDP, the other TCP/IP protocol which works at this level provides. With TCP, the application which sends the data receives acknowledgement or verification that the data was actually received.
-
User Datagram Protocol (UDP): UDP does not provide reliable data transport. No acknowledgements are transmitted.
The Application Layer (layer four)
The Application layer of the DoD model provides the following key capabilities:
-
Enables applications to communicate between each other.
-
Provides access to the services of the lower layers of the DoD model.
The Application layer of the DoD model is associated with the Session layer, Presentation layer, and Application layer of the OSI model.


Franklin Sterns
In a class I took in about 1990, the instructor showed us a Network packet trace with DoD encoded in every packet. He said that gave the DoD rights to examine every packet…everywhere. I have not been able to validate this information since.
What do you know of this?
cosmas chuwa
hello
really am appreciate your concern the layer, this ma first time 2 cross this page am really u.
ali
hello
it is immense pleasure for me know functioning knowledge about the layers,
this is my first message to you.
i do really applause your work .