How to Open TCP Ports in Windows
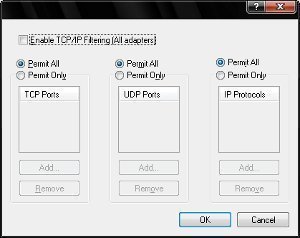
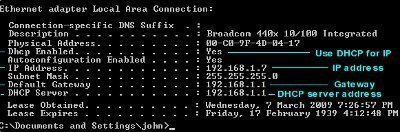
Opening TCP ports in Windows may be necessary for certain applications to run correctly. Each application may require a specific port to operate on. While a computer can and does open ports on its own, it may have to be done manually in certain situations. Here is a simple procedure. Step 1. Launch Windows and …