System Idle Process
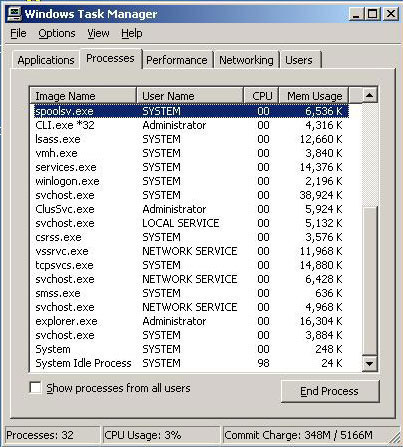
The System Idle Process on computers running the Microsoft Windows Operating System (OS) typically displays when it is using more than 90% of the computer’s CPU. This confuses many users as they believe that there is an OS error or more drastically that the computer is infected with malware. In reality, the System Idle Process …