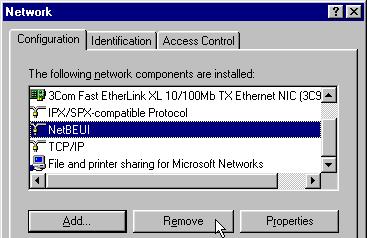
NetBEUI
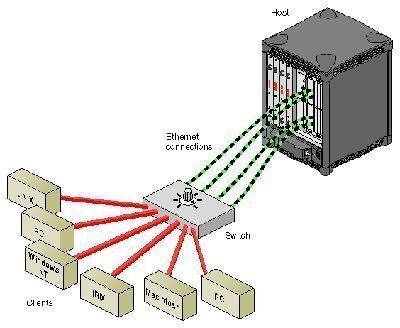
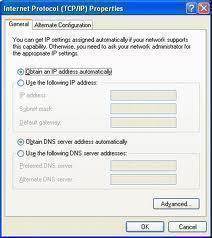
NetBEUI (NetBIOS Extended User Interface) is a program used for communication between applications installed on separate computers within the same LAN (Local Area Network). It is an upgraded version of NetBIOS and provides much more flexibility and functionality by rearranging the information in a data transmission. Like NetBIOS, NetBEUI is not a networking protocol and …