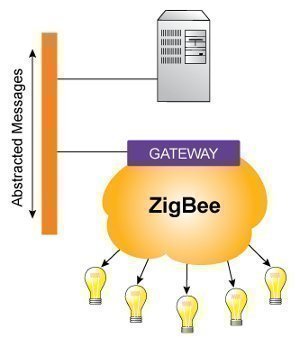
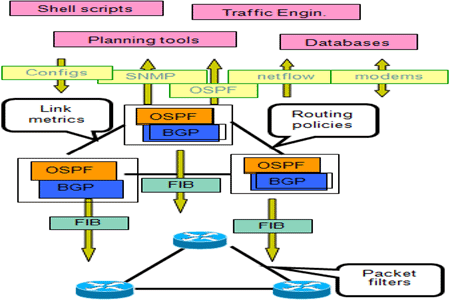
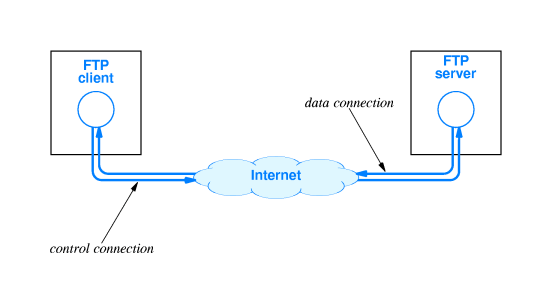
What is ZigBee?
ZigBee is a wireless protocol that was developed as an International standard to enable wireless, machine to machine communication, and networks. It is considered the catalyst for constructing “Smart” enabled buildings and homes since it is based on reliable network communications, a pro-longed battery life, and can be simply operated. The ZigBee Alliance is the …