How to Remove the Generic.dx Trojan
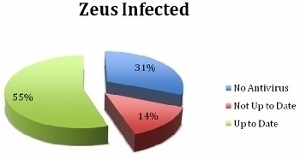
Generic.dx is a rather common trojan virus that infects the computer and weakens its security in order to allow other viruses and malicious software to infect the computer. It enters the computer via an email that the user opens, a website he/she visits, or a third party software that he/she downloads and installs. Generic.dx trojans …