Installing and Configuring NAT
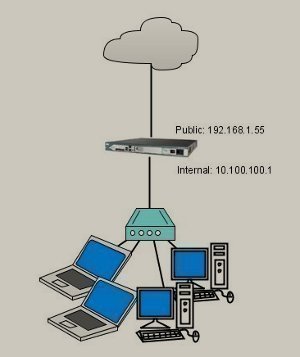
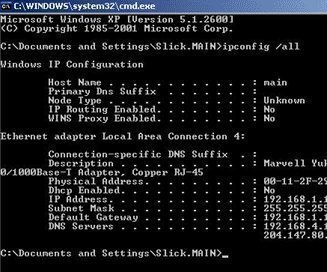
In Routing and Remote Access Service (RRAS), NAT can be used to provide basic Internet connectivity for small offices or home offices. NAT translates IP addresses and associated TCP/UDP port numbers on the private network to public IP addresses which can be routed on the Internet. Through NAT, host computers are able to share a …