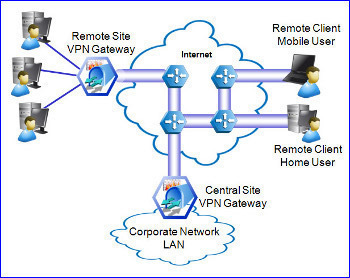
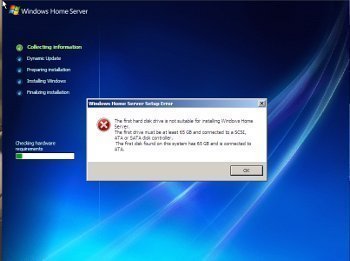
How to Fix a “Cannot Find Server or DNS” Error
A server is a computer that ‘serves’ the network that it is connected to. It performs functions that are useful to the network. For example, there are file servers that store data and print servers that handle the network printing jobs. Businesses and other institutions often use servers to store important, possibly confidential, information and …