A wide variety of Wi-Fi software tools are available. These tools for Wi-Fi perform functions such as:
- Wireless network discovery
- Wireless network mapping
- Wireless network traffic analysis
- Wireless network RF signal strength monitoring
- Wireless network encryption cracking
- Wireless network custom frame generation
- Dictionary or brute force attacks against wireless networks
- Denial of Service (DoS) attacks against wireless networks
These Wi-Fi software tools are available for a variety of platforms:
- Wi-Fi Software Tools for Multiple Platforms
- Wi-Fi Software Tools for Windows
- Wi-Fi Software Tools for Unix
- Wi-Fi Software Tools for Mac OS
- Windows tools useful when associated with Wi-Fi tools

Wi-Fi Software Tools for Multiple Platforms
Aircrack-ng
Aircrack-ng is a WEP and WPA-PSK key cracking program used on 802.11 networks. The primary purpose for the program is to recover a lost or unknown key once enough data is captured.
Aircrack-ng has the following advantages over the original Aircrack release:
- Updated and better documentation
- Updated drivers, including new drivers not originally supported in Aircrack
- New and faster WEP attack algorithm PTW
- Supports Unix, Windows, and Zaurus
- Includes fragmentation in attacks
- Better cracking performance
- Dictionary support for WEP attacks
- Uses multiple cards to capture simultaneously
- New tools including airtun-ng, packetforge-ng (improved arpforge), wesside-ng (still under development), and airserv-ng(still under development)
- Code optimizations and bug fixes
Wi-Fi Software Tools for Windows
KNSGEM II
KNSGEM II is a program that takes the survey logs that NetStumbler, Kismet, or WiFiHopper produces and compiles the data with data google earth to provide colorized 3D coverage maps.
NetStumbler
NetStumbler is a Wi-Fi tool for Windows that detects Wireless Local Area Networks (WLANs) using 802.11b, 802.11a, and 802.11g. It:
- Verifies that the network is set up as intended.
- Finds locations with poor coverage in the WLAN.
- Detects other networks that may be causing interference on the network.
- Detects unauthorized “rogue” access points in the workplace.
- Helps aim directional antennas for long-haul WLAN links.
- Uses it recreationally for WarDriving.
OmniPeek
Omnipeek is the next generation version of commercial wireless analysis software from wildpackets that combines the traditional applications, AiroPeek and EtherPeek.
OmniPeek features include the ability to:
- Analyze any network interface, including 10Gigabit, Gigabit, and WAN adapters
- Analyze media and data traffic simultaneously
- View results in normal document formats such as PDF, HTML, or just through email or IM clients
- View high level details of traffic in a dashboard or drill down into the individual packet payloads
- View local, remote, or previously stored captures (including multiple active captures at once)
- View capture details by conversation pairs to quickly identify useful or problematic events
- Change capture filters at will without restarting the capture sequence
Stumbverter
StumbVerter is a standalone application that allows users to import Network Stumbler’s summary files into Microsoft’s MapPoint 2004 maps. The logged WAPs are shown with small icons, their color, and shape relating to WEP mode and signal strength.
As the AP icons are created as MapPoint pushpins, the balloons contain other information, such as MAC address, signal strength, mode, etc. This balloon can also be used to write down useful information about the AP.
Lucent/Orinoco Registry Encryption/Decryption
Lucent Orinoco Client Manager stores WEP keys in the Windows registry under a certain encryption/obfuscation. This wi-fi tool can be used to encrypt WEP keys into a registry value or to decrypt registry values into WEP keys.
WiFi Hopper
WiFi Hopper is a Windows network discovery and connection client. It assists auditors with Site Surveys, Connection parameter testing, and Network Discovery. Filters allow users to easily limit the details displayed, as well as what kinds and configurations of equipment will be tested.
APTools
APTools is a utility that queries ARP Tables and Content Addressable Memory (CAM) for MAC Address ranges associated with 802.11b Access Points. It will also utilize Cisco Discovery Protocol (CDP) if available. If an Access Point that is web managed is identified, the security configuration of the Access Point is audited via HTML parsing.
Wi-Fi Software Tools for Unix
Aircrack
Aircrack is a unix static WEP and WPA-PSK key cracking utility. Aircrack is not under development anymore and Aircrack-ng has replaced it. Although functional, users should get aircrack-ng unless they have a specific reason to use aircrack.
Aircrack-ptw
Aircrack-ptw was a proof of concept software release showcasing the performance gains of implementing a new cracking algorithm. This toolset’s focus is on the WEP security algorithm. Aircrack-ptw is implemented in Aircrack-ng, which is a much more robust and complete package.
AirSnort
AirSnort is a wireless LAN (WLAN) tool that cracks encryption keys on 802.11b WEP networks. AirSnort operates by passively monitoring transmissions and computing the encryption key when enough packets have been gathered.
CoWPAtty
CoWPAtty is a program that utilized look up tables to optmize brute force key cracking for shortest time. The hash tables include 100,000 dictionary and common key words with the top 1000 most common WiFi SSIDs. The focus for cracking is on the WPA1 and WPA2 protocols. To crack a WEP key, try Aircrack-ng.
Karma
Karma is a set of wireless client assessment tools compiled into a single package release. The package’s intent is to identify and take advantage of operating systems that connect to access points. Although no exploit codes are provided with the code release, the suite has been tested with multiple exploit releases.
Kismet
Kismet is an 802.11 Layer 2 wireless network detector, sniffer, and Intrusion Detection System. Kismet works with any wireless card that supports raw monitoring (rfmon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic.
Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and decloaking) hidden networks, and inferring the presence of non-beaconing networks via data traffic.
Wellenreiter
Max Moser’s Wellenreiter is a GTK/Perl program that makes the discovery and auditing of 802.11b Wi-Fi wireless networks much easier. It supports all three major wireless cards (Prism2, Lucent, and Cisco). It has an embedded statistics engine for the common parametersthat wireless drivers provide. Its scanner window can be used to discover access-points, networks, and ad-hoc cards. It detects SSID broadcasting or non-broadcasting networks in every channel. The manufacturer and WEP is automatically detected. A flexible sound event configuration lets the user work in unattended environments. An ethereal / tcpdump-compatible dumpfile can be created for the whole session. GPS tracks the discovered networks’ location immediately. Automatic associating is possible with randomly generated MAC addreses. Wellenreiter can reside on low resolution devices that can run GTK/Perl and Linux/BSD (such as iPaqs). Uniq Essod-bruteforcer is now included too.
Airsnarf
Airsnarf is a simple rogue wireless access point setup utility that demonstrates how a rogue AP can steal usernames and passwords from public Wi-Fi hotspots. Airsnarf was developed and released to demonstrate an inherent vulnerability in public 802.11b hotspots–snarfing usernames and passwords by confusing users with DNS and HTTP redirects from a competing AP.
BSD-Airtools
BSD-airtools is a package that provides a complete toolset for wireless 802.11b auditing. It currently contains a bsd-based wep cracking application called dweputils (as well as kernel patches for NetBSD, OpenBSD, and FreeBSD). It also contains a curses based ap detection application similar to netstumbler (dstumbler) that detects wireless access points and connected nodes, view signal to noise graphs, and interactively scroll through scanned ap’s and view statistics for each. It also includes a couple other tools to provide a complete toolset for making use of all 14 of the prism2 debug modes as well as do basic analysis of the hardware-based link-layer protocols that prism2’s monitor debug mode provides.
WaveStumbler
WaveStumbler is a console based 802.11 network mapper for Linux.
WEPCrack
WEPCrack is a tool that cracks 802.11 WEP encryption keys by exploiting the weaknesses of RC4 key scheduling.
AirFart
AirFart is a wireless tool that detects Wi-Fi devices, calculate their signal strengths, and present them to the user in an easy to understand fashion. It is written in C/C++ with a GTK front end. Airfart supports all wireless network cards supported by the linux-wlan-ng Prism2 driver that provide hardware signal strength information in the “raw signal” format (ssi_type 3). Airfart implements a modular n-tier architecture with the data collection at the bottom tier and a graphical user interface at the top.
AirTraf
AirTraf is one of the first wireless 802.11(b) network analyzers. With the growth of interest in wireless networks, today’s network administrators are faced with a challenge. The challenge is to effectively deploy numerous access points within their organization to provide wireless coverage for all users and at the same time make sure that everyone who is granted access is able to operate in a fast, robust network environment.
AirTraf is a 100% passive packet sniffing tool for the wireless 802.11b networks. It captures and tracks all wireless activity in the coverage area, decodes packets, and maintains acquired information associated by access points as well as detected individual wireless nodes. It dynamically detects any access points in the area, finds association between wireless clients and access points, and builds an information table for each packet that is transmitted via the air. AirTraf is able to maintain packet count, byte information, related bandwidth, as well as signal strength of nodes.
Best of all, it is an open source and distributed under the GPL. Other comparable products that perform wireless network analysis price their products above $10,000 (such as Sniffer Wireless) and are limited to single licenses of copy, while AirTraf can be installed at any detection location, is enabled to run in Server Mode, and is polled periodically via the polling server to retrieve active wireless data from multiple stations at once. This results in the consolidation of wireless information over an entire organization into a single point of access (database). It can be administered via a web interface, at absolutely no cost to the organization.
However, AirTraf is still a work in progress, meaning that much of the planned features such as injecting packets into the network to test Access Point security, are not available yet. However, it is constantly being worked on, and soon it will prove to be a critical tool in managing healthy wireless networks in the future.
AP Hunter
AP Hunter (Access Point Hunter) can find and automatically connect to whatever wireless network is within range. AP Hunter can be used for site surveys and writes the results in a file.
AP Radar
AP Radar (Access Point Radar) is a Linux/GTK+ based graphical netstumbler and wireless profile manager. This project uses the version 14 wireless extensions in Linux 2.4.20 and 2.6 to provide access point scanning capabilities for most wireless card models. It is meant to replace the manual process of running iwconfig and dhclient. It makes reconfiguring for different wireless access points quick and easy.
Mognet
Mognet is a simple, lightweight 802.11b sniffer written in Java and available under the GPL. It features realtime capture output, support for all 802.11b generic and frame-specific headers, easy display of frame contents in hex or ascii, text mode capture for GUI-less devices, and loading/saving capture sessions in libpcap format.
PrismStumbler
Prismstumbler is a wireless LAN (WLAN) discovery tool that scans for beaconframes from accesspoints. Prismstumbler operates by constantly switching channels and monitors any frames received on the currently selected channel.
Prismstumbler is a flexible tool to find as much information about wireless LAN installations as possible. It comes with an easy to use GTK2 front end and is small enough to fit on a small portable system. Because of its client-server architecture, the scanner engine may be used for different front ends. An example of this is gpe-aerial, a wireless LAN access tool for GPE.
The current GTK user interface works on large PC screens as well as PDA displays. Prismstumbler uses an embedded SQL database to store network information. It is also able to create network lists in GPSdrive format and store captured packages to pcap dump files.
THC WarDrive
THC-WarDrive is a tool for mapping a city for wavelan networks with a GPS device while driving a car or walking through the streets. It is effective and flexible, a “must-download” for all wavelan nerds.
Wifi-Scanner
Wifi-Scanner is a tool that has been designed to discover wireless nodes (i.e access point and wireless clients). It is distributed under the GPL License.
WiFi-Scanner works with Cisco cards and prism cards with the hostap driver or wlan-ng driver.
An IDS (Intrusion Detection System) is integrated into Wifi-Scanner to detect anomalies like MAC usurpation.
WaveMon
Wavemon is a ncurses-based monitor for wireless devices. It allows users to watch the signal and noise levels, packet statistics, device configuration, and network wireless network hardware parameters.
asleap
asleap exploits weaknesses in Cisco’s LEAP protocol. Specifically, asleap:
- Recovers weak LEAP passwords.
- Can read live from any wireless interface in RFMON mode.
- Can monitor a single channel or channel hop to look for targets.
- Will actively de-authenticate users on LEAP networks, forcing them to re-authenticate. This makes the capture of LEAP passwords very fast.
- Will only deal with users who have not already been seen, does not waste time on users who are not running LEAP.
- Can read from stored libpcap files or AiroPeek NX files (1.X or 2.X files).
- Uses a dynamic database table and index to make lookups on large files very fast. Reduces the worst case search time to .0015% as opposed to lookups in a flat file.
- Can write *just* the LEAP exchange information to a libpcap file. This captures LEAP credentials with a device short on disk space (like an iPaq), then processes the LEAP credentials stored in the libpcap file on a system with more storage resources.
anwrap
anwrap.pl is a wrapper for ancontrol that serves as a Dictionary attack tool against LEAP enabled Cisco Wireless Networks. anwrap traverses a user list and password list attempting authentication and logging the results to a file. anrwap really wreaks havoc on RADIUS calls to NT networks that have lockout policies in place. Users should tweak the Timeouts as a lengthy LEAP timeout on the Cisco side could make for a very boring afternoon. anwrap audits authentication strengths before deploying LEAP in a production environment.
WAP Attack
WepAttack is a WLAN open source Linux tool for breaking 802.11 WEP keys. This tool is based on an active dictionary attack that tests millions of words to find the right key. Only one packet is required to start an attack.
WEPWedgie
WEPWedgie is a toolkit for determining 802.11 WEP keystreams and injecting traffic with known keystreams. The toolkit also includes logic for firewall rule mapping, pingscanning, and portscanning via the injection channel and a cellular modem.
AirJack
AirJack is a device driver (or suite of device drivers) for 802.11(a/b/g) raw frame injection and reception. It is meant as a development tool for all manner of 802.11 applications that need to access the raw protocol.
void11
ivoid11 is a free implementation of basic 802.11 attacks:
- deauth (Network DOS) (flood wireless networks with de-authentication packets and spoofed BSSID; authenticated stations will drop their network connections)
- auth (Accesspoint DOS) (flood accesspoints with authentication packets and random stations addresses; some accesspoints will deny any service after some flooding)
- Apple Airport aka “UFO” died after ~60sec flooding for about 15 minutes
- Lucent OR1000 survived with minor problems
- OpenBSD 3.1/3.2 HostAP freezed after some flooding
- Linux HostAP driver survived (max. 1023 authenticated stations)
Wireless Access point Utilities for Unix
Wireless Access Point Utilities for Unix is a set of wi-fi utilities to configure and monitor Wireless Access Points under Unix with SNMP protocol. GCC and IBM C compiler compiles Wireless Access Point Utilities and runs under Linux, FreeBSD, NetBSD, MacOS-X, AIX, QNX, and OpenBSD.
APTools
APTools is a utility that queries ARP Tables and Content Addressable Memory (CAM) for MAC Address ranges associated with 802.11b Access Points. It also utilizes Cisco Discovery Protocol (CDP) if available. If an Access Point that is web managed is identified, the Access Point’s security configuration is audited via HTML parsing.
gpsd
gpsd is a daemon that listens to a GPS or Loran receiver and translates the positional data into a simplified format that other programs, like chart plotters, can more easily use. The package comes with a sample client that plots the currently visible GPS satellites’ location (if available) and a speedometer. It can also use DGPS/ip.
GpsDrive
GpsDrive is a car (bike, ship, plane) navigation system. GpsDrive displays the car’s position via an NMEA capable GPS receiver on a zoomable map. The map file is auto selected depending on the position and preferred scale. Speech output is supported if the “festival” software is running. The maps are auto selected for best resolution depending on the car’s position and can be downloaded from the Internet. All Garmin GPS receivers with a serial output and other GPS receivers that support NMEA protocol should be usable.
airpwn
Airpwn is a tool for generic packet injection on an 802.11 network.
airpwn requires two 802.11b interfaces: one for listening and another for injecting. It uses a config file with multiple config sections to respond to specific data packets with arbitrary content.
Wifitap
WifiTap allows users to connect to wifi networks with traffic injection. The concept is the same as most “man-in-the-middle” or “monkey-in-the-middle” attacks. For WifiTap to work, another system must have an association with an access point that the WifiTap system wants to pass traffic through.
Benefits of using WifiTap rather than normal Wifi clients:
- The system running wifitap is not associated with any wireless access point
- Access points do not handle the system.
Wi-Fi Software Tools for Mac OS
MacStumbler.
MacStumbler is a utility that displays information about nearby 802.11b and 802.11g wireless access points. It is a tool to help find access points while traveling or to diagnose wireless network problems. Additionally, MacStumbler can be used for “wardriving,” which involves coordinating with a GPS unit while traveling around to help produce a map of all access points in a given area.
KisMAC
KisMAC is a free stumbler application for MacOS X that puts the user’s card into the monitor mode. Unlike most other OS X applications, KisMAC is completely invisible and sends no probe requests. KisMAC supports third party PCMCIA cards with Orinoco and PrismII chipsets, as well as Cisco Aironet cards.
Kismet
Kismet is an 802.11 Layer 2 wireless network detector, sniffer, and Intrusion Detection System. Kismet works with any wireless card that supports raw monitoring (rfmon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic.
Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and given time, de-cloaking) hidden networks, and inferring the non-beaconing networks’ presence via data traffic.
Windows Tools that are Useful when Associated with Wi-Fi tools
MacIdChanger
MacIdChanger allows users to easily and temporarily change the the windows network adapter’s MAC Address. This generally conceals the unique mac id that is on every network adapter. This software only operates on Windows XP/2003.
Technitium MAC Address Changer
This is a free, very verbose, and functional tool to change network adapters’ MAC Address. The tool works regardless of which network adapter or driver is installed in a system. Supported platforms are Windows NT, Windows 2000, Windows XP, and Windows Vista.

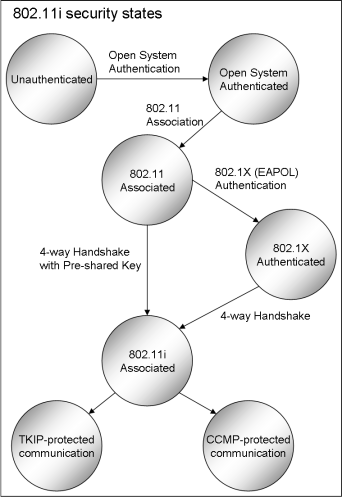
azaki
Hi,
Is there a tool to discover lightweight AP’s and be able to poll information that includes uptime value from them via SNMP?
thanks,
Azaki
Jeff
I work at a hotel where we offer registered guests free wifi. Problem is that there are so many scam SSIDs that show up in the available wireless network table our guests often have problems finding and connecting to our network (we do have a logon and password the guest receives at check-in). Sometimes our SSID shows up so far down in the list that users have to scroll to find us. We have 54 HP ProCurve MSM310 APs about the property amd put out a strong signal. Is there anything out there that would allow me to block the rogue SSID signals coming into this hotel or make my SSID show up higher on the list? I can’t very well ask every guest to install some kind of software or instruct each one how to filter out the bad networks. Many of these SSIDs do absolutely nothing while others try to get a credit card number.
Very frustrating and wasting a lot of my time.
Owen
Hi Paul,
That’s an easy fix, provided the internet cafe will tell you the Access Point’s Mac Address. If so, you can bind your network to *only* that AP. (I can do this on my laptop – what OS are you using?)
Owen
I should also add that (from memory) most network sniffers can tell you the MAC address of a particular AP, so you could find it out yourself using one of the tools above.
Kailash
Dear Allm
we need wi-fi access points information.
wi-fi access pointwise how access point connected in network
in access point which users is connected in AP
every in one windows information.
how can do that please give me soulation.
Parveen
How to detect other downloads activate on the same network connected through wi-fi plz tell me how to deactivate and activate donloads on other pcs…..plz plz help me
Stephen
I would like a utility that records the traffic load sent to a known router from a second wlan device. I have reason to believe that my ISP is over charging my usage by about a third and would like evidence to support this.
Can anyone reccomend a tool which can do this or easily modifiable to perform this task?
Thanks.
Kevin L
I will add Maxidix Wifi Suite, this tool is really help me. It brings all the info about wifi, makes easy to find and manage networks and many other. Its free trial.
kami
tnx alot , cool collection
ömer
tşk ederiz de türkiye de forumların konusu olmus.
easy radar programı tarzında modem yeri gösteren yazılım yok mudur
Thomas Kb
This is really a usefull information
memenode
Fixed, among other broken or outdated links.
Thanks!