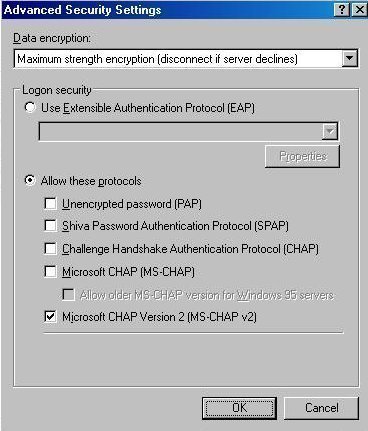
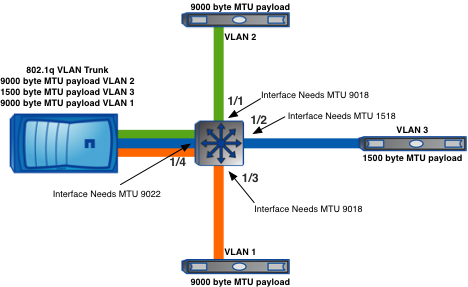
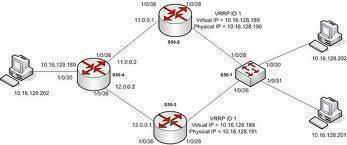
Interior Gateway Routing Protocol
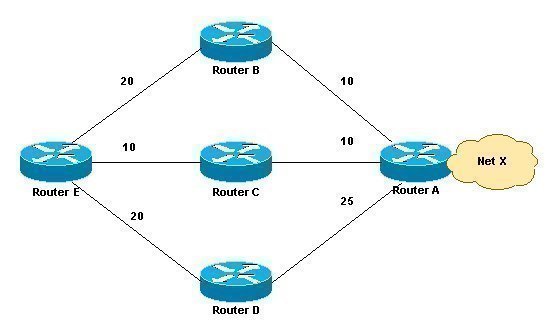
The Interior Gateway Routing Protocol (IGRP) is a network routing protocol that is designed to enable routing inside of an Autonomous System (AS). Cisco developed this protocol in the late 1980s in response to the existing Routing Information Protocol’s (RIP) shortcomings. As Cisco routers became more popular, a number of large networks began using IGRP, …