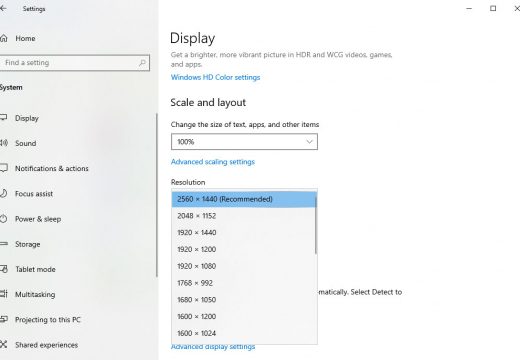
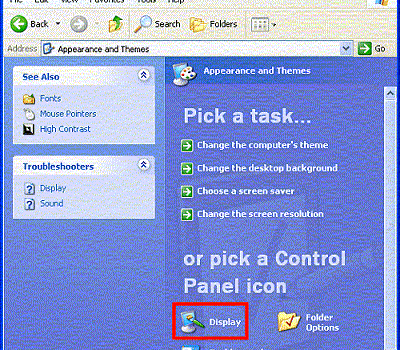
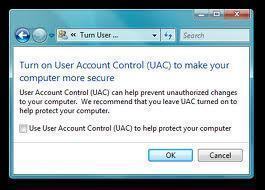
How to Change Resolution in Windows 10?
Screen resolution is a number of pixels (small dots) your screen has horizontally, multiplied by the number of pixels vertically. The more pixels you have, the better the quality of the image. Resolution numbers are represented in the following formats: 800×600, 1024×768, 1366×768, 1600×900, 1680×1050, 1920×1080, 2560×1440 and so on… In practice, lower resolution means that …